Hacking is one of the largest growing problems for Governments, businesses, and individuals. In early 2014 the department store “Target”, was hacked in one of the largest data breaches in history; According to Brian Krebs (2014) upon further investigation it is believed the hack was carried out by Russians using an exploit developed for their particular Point of-Sale system. Olenick (2014) reports the estimated losses due to this breach at $450 million. Hacking has become such a big problem that FBI Director James Comey, at a press conference in Boston was quoted saying, “All of us have connected our entire lives to the Internet… anybody who will hurt us, that is where they will come.” Cybercrime is no longer just considered a crime, it is increasingly considered by the Government as “Cyber-terrorism”, which is one of the two biggest threats to National Security along with homegrown terrorism. (Castellanos, 2014)
With this ever-increasing issue it is important to understand just how these attacks are carried out as well as the motives behind the individual or group.
The term “hacker” has changed over the years from someone who pushed technology beyond its limits and broke security implementations, to someone who is malicious and breaks into systems. The correct term for criminals who use hacking techniques to commit crimes are “crackers”. Since this term is rarely used even by Government agencies, crackers will be referred to as hackers in this paper.
Hacktivism relates to the idea that the motivation to hack a target comes from a political ideology instead of monetary gain. Hacktivism is an issue that has gained a significant amount of media attention in the past few years; one of the largest hacktivist groups known as “Anonymous” has been credited with performing hacks against groups such as the white supremacy group, “The KKK” to religious extremist group, “The Westboro Baptist Church”. Hacktivism has caused an ethical dilemma as these attacks gain positive attention from social media, which further motivates individuals or groups to keep attacking targets believing that they are above the law.
The issue with these hacktivism groups is that the individuals that join these groups vary significantly in age, skill, and even political ideologies. This results in kids and teenagers being arrested after participating in hacking attacks because they are not skilled enough to cover their tracks, and often rely on easy to use tools found on the internet such as Low-orbit ion cannon (LOIC); a network stressing tool that floods a server with UDP/TCP packets causing all the bandwidth of the server to be used up, denying actual users from accessing it. (Hunt, 2013) A single person using this program would likely not do much damage at all to a large website since an individual’s resources are limited, but 300+ computers running this program can cause a server to be crippled which is referred to as a “Distributed Denial of Service Attack” (DDoS) since multiple computers are used at once either manually or chained together in what is known as a “botnet”.
Botnets are very difficult to track and takedown since they are usually comprised of infected computers from all over the world; finding who is controlling them is next to impossible since they can just route their connections through several infected computers from all different parts of the world. The FBI isn’t welcome in every country to investigate so many leads can just be lost because they can’t gain access to a computer. However in 2013 the FBI carried out one of the largest Cyber Crime Operations that stretched across multiple countries to disrupt a piece of black market malware known as “Citadel”; created by an anonymous entity called “The Poetry Group”, which infects computers and allows complete remote connectivity.
FBI Executive Assistant Director, Richard McFeely (2013) reported that the FBI had disrupted over 1,000 machines infected but still never found the individual(s) that created the piece of malware in the first place. Despite this large operation, Ryan Sherstobitoff (2013) of McAfee Labs reported that the malware is still active with over 500 detected infections in Europe with the largest amount of infection in Poland. The still active infections raises the question of is money still being made for the Poetry Group? This leads to the next motivation of hackers which is monetary gain.
It is suspected that in China hacking is a state sponsored activity to steal company secrets about microchips, computer networking equipment, and data storage services. China has some of the most skilled hackers in the world; developing many “zero-day” exploits to either sell them to others or use them to steal data. Zero-days refer to exploits (security holes) that developers are unaware of and therefore don’t have enough time to patch them as soon as the exploit is released. These can sell for millions of dollars since millions more can be stole within the matter of minutes. (Strohm, 2014)
Another large section of for-profit hacking is the PC gaming industry. Online game items such as armor and weapons now have monetary value to gamers that can sell for hundreds of dollars. Hackers typically use what is known as phishing sites or key loggers to steal gamer credentials. Phishing sites are set up to look exactly like the real thing, usually a scammer will send a link to a site that URL looks like a legitimate trading site such as below:
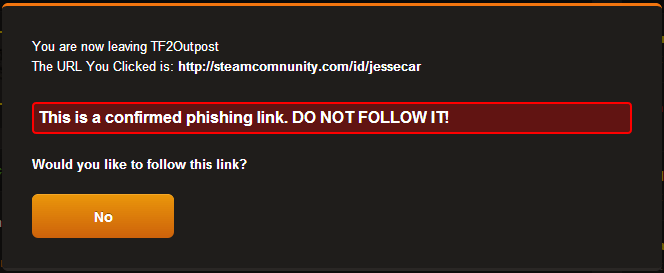
(Image Source: http://cloud-2.steampowered.com/ugc/703984919083425794/8459025DD2F7BBEC29192C50807AB4349EEDE59A/)
The original link is supposed to be “steamcommunity.com” but if you look closely you can notice that there is a spelling error, the average user would probably not even notice if a security warning didn’t pop up. These phishing sites often use a tool called “Social Engineering Toolkit (SET)”, which is part of the Penetration Testing OS known as “Backtrack”. This tool has the capability to make an exact clone of the website and replace the database with a plain-text one that the attacker can view to take the credentials (login details). The more sophisticated ones can actually steal the credentials then redirect to the intended site so the victim never knows that he or she was phished. (Mohamed, 2013)
Another popular method for stealing these credentials is the use of key loggers. Krebs (2010) writes that these key loggers are usually bundled together with freeware or pirated programs then unsuspectingly installed by users. Once installed they record every keystroke pressed on the keyboard and can either store the data locally in a text file to be retrieved physically, or more commonly are sent over the internet to either directly to the attacker’s computer or a remote server so the attacker can’t be traced. This method is also commonly used for corporate espionage but instead of software, a piece of hardware is used that is plugged into the back of the computer in between the computer and the keyboard that does the same function as a software key logger. The advantage to this method is that it requires very little time to install and offers the littlest amount of risk for detection by anti-virus. The data is retrieved by simply unplugging the device and plugging it into another computer to view its contents. An image of this hardware is below:
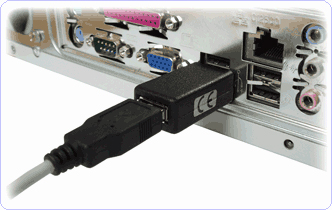
An increasing amount of attacks are using what is known as “SQL Injection”, these attacks manipulate SQL databases that have been improperly set up by using a web page input on the site and inputting commands such as “SELECT UserId, Name, Password FROM Users WHERE UserId = 105 or 1=1”. This is a normal SQL statement requesting the User Id, name, and password. However “UserId = 105 or 1=1” can give out the whole table since 1=1 is always a true statement. Of course the average database administrator should be able to setup the SQL database so this won’t work, but there are countless amounts of queries that can be given, making sure that an every single statement won’t accidentally reveal access to a restricted part of the database is a tough challenge. One method some web developers use to stop this is by using blacklists of words not allowed to be searched for, which stop attacks but also can cause some significant problems for normal operation of the database since some words need to be used. (SQL Injection, n.d)
Mischief is a large motivator to many hackers; it is a form of entertainment to some even though it often results in monetary loss to the victim. Generally the hackers who participate in this mischief are of lower skill and referred to as “script-kiddies” by the hacking community. Script-kiddie is a derogatory term for someone with little to no technical or programming experience that relies on easy-to-use hacking software that is either free or paid-for. Extremely malicious examples of the software used by these hackers are known as “RATs” (Remote Access Trojans), that are typically installed by convincing a victim to click a .exe program or open an infected PDF. Once the software is installed the attacker has complete control of the victim’s computer. A popular paid-for RAT known as “Black shades”, which Sullivan (2014) reports resulted in the arrest of 24-year old Swedish man “Alex Yucel” and many users of it, had the ability for the attacker to spy through the victims webcam, listen through the microphone, access every file, look at keystrokes, and even open up the disk tray.
It is very easy for antiviruses to detect RATs because of their highly intrusive nature, but when combined with a “Crypter” they still pose a serious threat. Crypters take an infected file such as a RAT and encrypt it into a “stub” which looks like a normal program so when it is scanned by anti-virus it comes out clean then proceeds to infect the computer. The more advanced crypters can disable real time virus protection or “melt” the stub, meaning the stub will erase itself after a period of time but the computer will continue to be infected. Sometimes these malicious files are so well hidden that a complete factory reset won’t even clear them since they can infect recovery files as well. (How Does a Crypter Work?, 2010)
Technology is increasing rapidly and becoming more and more intertwined into every aspect of daily life. The presence of high-tech hackers poses a great threat to everyone who uses technology; lives can be ruined, money can be stolen, and even lives can be lost due to information being leaked. The temptations of money and fame are tempting to even the most educated Computer Science/Information Technology individuals but it is important to remember that just because a screen and keyboard is used instead of a gun or burglary tool doesn’t make it anymore justifiable. The methods of hacking are just going to get more sophisticated and hard to prevent as time goes on so the need of Information Security individuals is going to be in ever increasing demand for the foreseeable future.
References
Castellanos, S. (2014, November 19). FBI director: Cyber threats are moving ‘at the speed of light’ – Baltimore Business Journal. Retrieved November 20, 2014, from http://www.bizjournals.com/baltimore/blog/cyberbizblog/2014/11/fbi-director-cyber-threats-are-moving-at-the-speed.html
How Does a Crypter Work? (2010, June 6). Retrieved November 20, 2014, from http://www.crypters.net/crypter-info/how-does-a-crypter-work/
Hunt, T. (2013, January 29). What is LOIC and can I be arrested for DDoSing? Retrieved November 20, 2014, from http://www.troyhunt.com/2013/01/what-is-loic-and-can-i-be-arrested-for.html
Krebs, B. (2010, June 14). Cloud Keyloggers? Retrieved November 20, 2014, from http://krebsonsecurity.com/2010/06/cloud-keyloggers/
Krebs, B. (2014, February 14). Target Hackers Broke in Via HVAC Company. Retrieved November 20, 2014, from http://krebsonsecurity.com/2014/02/target-hackers-broke-in-via-hvac-company/
McFeely, R. (2013, June 5). FBI Statement on Botnet Operation. Retrieved November 20, 2014, from http://www.fbi.gov/news/news_blog/botnets-101/fbi-statement-on-botnet-operation
Mohamed, A. (2013, June 19). Phishing and Social Engineering Techniques 3.0. Retrieved November 20, 2014, from http://resources.infosecinstitute.com/phishing-and-social-engineering-techniques-3-0/
Olenick, D. (2014, February 16). Target’s loss to credit thieves could be up to $450 million, Q4 earnings take a hacking. Retrieved November 20, 2014, from http://www.techtimes.com/articles/3794/20140226/target-loss-to-credit-thieves-pegged-at-400-million-q4-earnings-take-a-hacking.htm
SQL Injection. (n.d.). Retrieved November 20, 2014, from http://www.w3schools.com/sql/sql_injection.asp
Sherstobitoff, R. (2013, February 19). Inside the World of the Citadel Trojan. Retrieved November 20, 2014, from http://www.mcafee.com/us/resources/white-papers/wp-citadel-trojan.pdf
Strohm, C. (2014, October 16). FBI Warns Tech Companies of State-Sponsored China Hackers. Retrieved November 20, 2014, from http://www.bloomberg.com/news/2014-10-16/fbi-warns-of-chinese-hackers-attacking-tech-companies.html
Sullivan, G. (2014, May 20). 5 scary things about the ‘Blackshades’ RAT. Retrieved November 20, 2014, from http://www.washingtonpost.com/news/morning-mix/wp/2014/05/20/5-scary-things-about-blackshades-malware/
