Phishing attacks are hands down the most successful form of hacking there is, they rely on fooling a person that they are accessing a trustworthy website where they can enter in sensitive information such as credit card numbers, social security numbers, banking info, etc. when in reality they are using a fake website that looks identical to the real thing and anything they submit through that website goes right to the hacker.
These attacks work so well because they can look so authentic, take for example this email disguised to look like it is from Netflix:
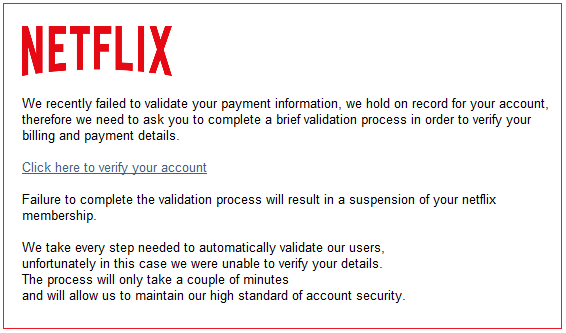
It sounds valid, it looks valid, and for hundreds of thousands of people they believe it IS valid. Then once your credit card details are given they might even make it seem more believable by saying something to the extent of “Thank you for validating your payment info, your account suspension is now lifted” so people do not go and cancel their credit cards immediately after. Hackers with this data then turn to the “Dark Web” to sell this sensitive info to the highest bidder.
I feel it is important to give a brief explanation of the Dark Web. It is a subject that not many people like to address because of the many illegalities associated with it, however it is important to understand how deep it truly goes and how it works to get a glimpse into what motivates hackers and how they get away with their crimes.
The Dark Web today is mostly based around “.onion” sites which are long random character string URLs that can only be accessed using the TOR browser. The TOR browser anonymizes a person’s connection to the .onion sites by routing the traffic through multiple different nodes (servers) so the person’s original IP address is never revealed, this makes it great for hackers to conduct business since it allows them to avoid law enforcement. On the dark web sensitive information is bought and sold using Bitcoin; a cryptocurrency that I will eventually cover. A large portion of these illegal goods are bought and sold by Russian hackers.
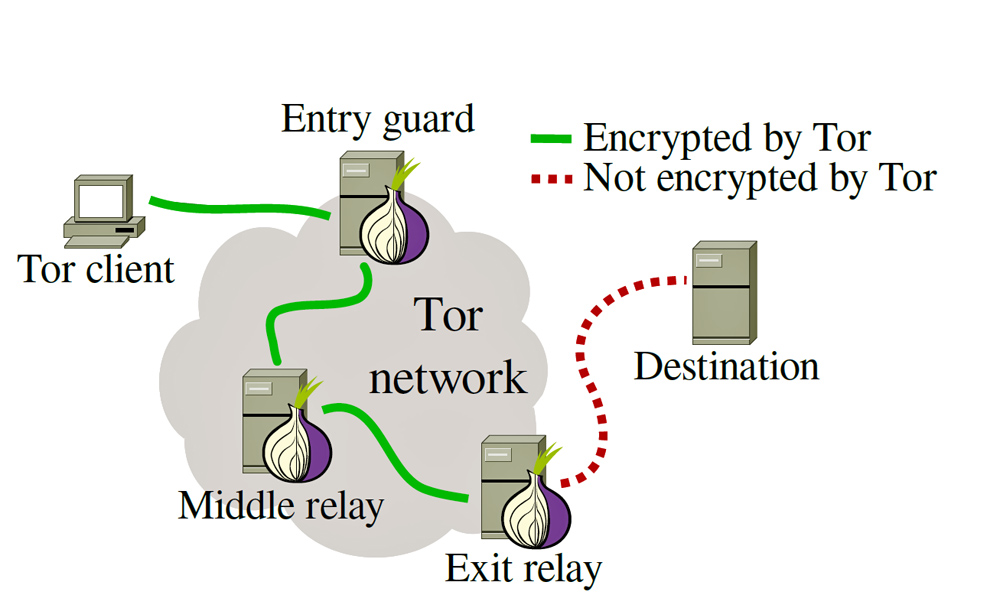
I relate this information to phishing because many people’s first reactions to having sensitive information stolen from them is “who have I met that has done this to me?” when the truth is your info may have been bought and sold multiple times before anyone tried to do anything to it. Rarely are hackers dumb enough to directly use information they have stolen, but that is not to say it does not happen.
What can I do to protect myself from Phishing attacks?Never open a link from an email address you are not 100% you know is correct.
- Check the spelling carefully, looking for things like paypa1.com where letters are substituted as numbers and vice versa.
- If you see spelling errors or strange grammar contained within the email do not open.
Professional businesses rarely make typos and grammatical errors, and since many hackers are foreign they do not have a great grasp on the English language. If you are in America also look out for the European spellings of words as a red flag since many hackers learn European English.
3. If you do click on the link and it brings you to a website, check the URL carefully and also look for a green lock to the left of the URL.
The green lock represents that it is a secure site, a red lock or no lock means that it could be potentially insecure, and again check the spelling of the website to make sure it is correct.
- Use a VPN if you need to connect to the internet on a public network such as an airport or library.
Hackers on the same network can spoof what is called a “DNS Server” that tells your computer how to directly connect to websites and change it so you are re-routed to the hacker’s fake page.
2. The most fool proof way to avoid this by far is to never click links in emails and instead type the website directly into your search bar.
Websites such as Netflix and Amazon will tell you if there is a payment problem when you login to your account, there is no need to do it from an email.
3. If you are part of a large company inform your employees to be vigilant against phishing attacks.
Many people may have heard about phishing attacks in the news but still do not understand what they exactly are, a brief 30 minute presentation once a year on digital security can help immensely in reducing risks.
- Install some browser plugins to help protect you.
- uBlock Origin for Google Chrome keeps a list of known malware sites to block.
- HTTPS Everywhere for Google Chrome forces your connection to use SSL encryption technology (if supported by the website).
Spreading awareness of this attack method is very important since government and law enforcement employees still fall victim to it every day. Phishing techniques can vary in sophistication and method but I have tried to lay out the most used ones, if you have any questions feel free to write them in the comments.
