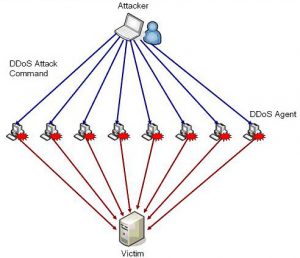
DDoS stands for “Distributed Denial of Service”, which is the more harmful cousin of DoS “Denial of Service”. The distributed part means that the attack is being carried out on multiple computers, usually spread across the nation or world. These attacks are very simple in nature but very difficult to stop, think of these attacks similar to if you kept calling a local pizza place than hung up every time someone answered. These calls would deny other customers from placing their order because you were constantly tying up the phone line. Say the pizza place had an option to block your calls based on your phone number, the lines could be free again and people could order their pizzas. That is an example of a single DoS attack, however a DDoS attack would be if you had access to hundreds of different phone numbers to call the pizza place so the pizza place would not be able to distinguish if the caller wanted to place a legitimate order or was a part of this attack.
Source: www.niiconsulting.com
These attacks on websites and servers are very similar to this pizza place metaphor, attackers have access to what is known as “botnets” which are infected computers that they control to spam websites and servers with bogus “packets” (chunks of data). The result of this is either the server becomes very slow, inaccessible to legitimate users, or in the worst case completely crashes. As you might imagine firewalls try to filter out these packets and may succeed but the problem still remains that even blocking these requests takes up processing resources of the firewall which may eventually crash or overwhelm the firewall, causing it to stop functioning properly.
What can be done?
- Buy more bandwidth for your server or website to hopefully prevent slowdowns from the attacks.
- Set up routers and firewalls to block packets from known sources of attacks and obvious attack patterns.
- Call your ISP (Internet Service Provider) to explain the situation and see if they can take any action including mitigation.
- Hire a mitigation company such as Cloudflare or Akami who takes the brunt of the attack on their servers then filters out legitimate traffic to yours. (These can be very costly but worth every penny if you’re on online merchant and stand to lose thousands for every second your servers are down).
In my opinion these attacks will only get worse in time as bandwidth availability is steadily increasing all over the world and the generation of hackers are becoming more clever and brilliant every day.
