I woke up around 1pm after a long night (or morning really) until 6am writing a paper, when I reached over to shut off my alarm I noticed “266 new emails” on my phone. Thinking this was some kind of bug on my phone I swiped the notification away until I had a cup of coffee and sat down at my computer, opened up my email, and realized that there was indeed an overwhelming amount of emails from the plugin I use to supplement security on my WordPress site called “iThemes Security”.
The emails all contained different IP addresses that had tried to brute force their way into my WordPress login page only to be locked out after 10 attempts by my plugin. My immediate thought was “I’m lucky to get 300 unique users a month, where did all these people find my website?” I might inspire to be Brian Krebs, but I have never poked around a hornets nest like he has.
I started doing IP lookups on the attackers and could not notice any trend at all. I was seeing attacks from Jordan, Israel, Houston, Toronto, Bolivia, Turkey, Japan, Belgium, Romania, Bulgaria, Mexico, Nepal, and most interesting to me: Madagascar. I quickly realized the culprit after some Google searching, there is a massive botnet of around 90,000 computers attacking WordPress sites through bruteforce attacks. In my opinion that number is likely to be much higher.
Equipped with a VPN and Kali Linux inside of VirtualBox I decided to use nmap to port scan the most recent IP address originating from Ankara, Turkey.
My first scan was:
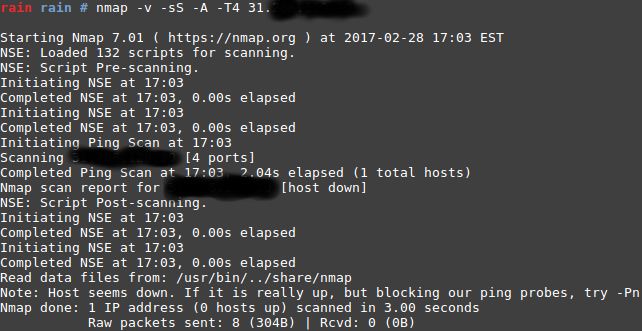
As you can see from the output I was blocked from receiving any info so I used the -Pn flag since the firewall was most likely blocking me from any info. Here is one thing I found interesting from the results:
![]()
Upon looking up port 1050 I came across this on speedguide.net:
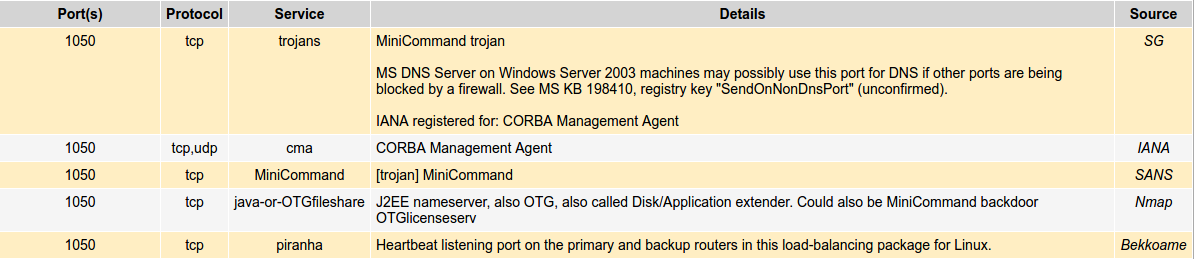
The service on port 1050 “java-or-OTGfileshare” could possibly be a trojan called “MiniCommand”, of course this is just speculation and some circumstantial reasoning. To confirm this port info was associated with the MiniCommand Trojan I also found the same information included in David J. Marchette’s book “Computer Intrusion Detection and Network Monitoring: A Statistical Viewpoint”. (Page 267)
I then found a description of this trojan that was very general by Snort, a Cisco research company:
Impact
Possible theft of data and control of the targeted machine leading to a compromise of all resources the machine is connected to.
Detailed information
Trojan horse programs can be used by an attacker to steal data from the infected machine, they can also be used to control the infected host. This event indicates that activity relating to the trojan horse program minicommand has been detected in network traffic.
Affected systems
- Microsoft windows systems
Attack scenarios
This Trojan may be delivered to the target in a number of ways. This event is indicative of an existing infection being activated. Initial compromise can be in the form of a Win32 installation program that may use the extension “.jpg” or “.bmp” when delivered via e-mail for example.
From my research further into the history of this trojan, it looks to be from the 2000-2006 era with it primarily effecting Windows XP machines. This might seem crazy to still be in existence but according to Scott Berker of Redmonnd Magazine, “250 million users are still actively using Windows XP.”
That’s an incredible number of PCs that can be hacked with no problem and be turned into zombie computers.
The MiniCommand trojan might not be responsible for the source of these attacks in whole, but there is a good chance that a combination of different trojans are responsible for this enormous botnet problem.
This is the first article of this sort I have attempted to publish, I would appreciate any opinions, suggestions, theories, or corrections you may have.
